14) which of the following are breach prevention best practices
Identity sensitive data collected stored transmitted or processes. Preventing HIPAA Data Breaches.
Preventing Hipaa Data Breaches Case Studies And Best Practices
10 The HIPAA Security Rule applies to which of the following.

. 1 In 2017 healthcare data breaches compromised more than 5 million healthcare records 2. Which of the following are breach prevention best practices. Which of the following are examples of personally identifiable information PII.
Which of the following statements about the HIPAA Security Rule are true. All of the above. Loss of customer trust brand damage reputational harm legal exposure and higher costs.
In a hyper-connected business world organizational leaders understand that data breaches are a fact of life. Which of the following are examples of personally identifiable information PII. Access only the minimum amount of PHIpersonally identifiable information PII necessary Logoff or lock your workstation when it is unattended Promptly retrieve documents containing PHIPHI from the printer All of this above 15 An incidental use or disclosure is not a.
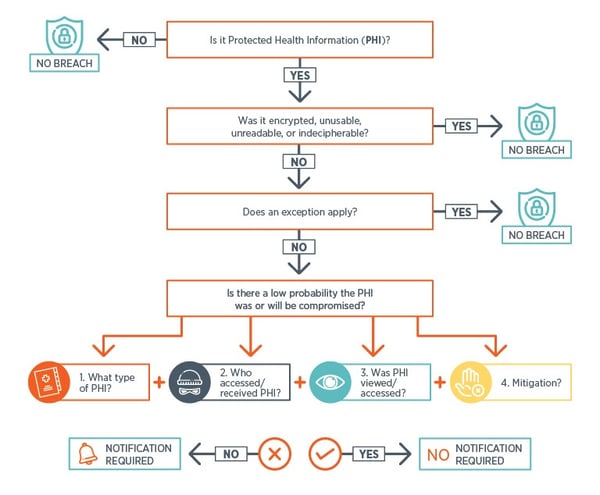
Breach Notification Rule - 45 CFR 164400-414 If an impermissible use of disclosure of PHI is determined to be a Breach CEs must provide notification of the Breach to affected individuals the Secretary of HHS The Secretary state entities under applicable state law and in certain circumstances to the media Reputation. These practical user-friendly guides can help your practice facilitate the adoption of standards-based approaches to cybersecurity. 1800-4 Mobile Device Security.
Companies that leveraged artificial intelligence machine learning analytics and automated. Remediation Accessed N PHI transmitted orally PHI on paper PHI transmitted electronically correct All of the above-----11 Which of the following are breach prevention best practices. Which of the following are breach prevention best practices.
A Access only the minimum amount of PHIpersonally identifiable information PII necessary b Logoff or lock your workstation when it is unattended c Promptly retrieve documents containing PHIPHI from the printer d All of the above. Access only the minimum amount of PHIpersonally identifiable information PII necessary Logoff or lock your workstation when it is unattended Promptly retrieve documents containing PHIPHI from the printer All of this above 15 An incidental use or disclosure is not a. Which of the following are breach prevention best practices.
All of the above answer a. Before you can prevent a data breach. The publications with specific applicability to healthcare are.
The Five Most Frequently Asked Questions About Data Breach Recovery. Case Studies and Best Practices. Which of the following are breach prevention best practices.
True False 14 Which of the following are breach prevention best practices. True False 14 Which of the following are breach prevention best practices. A Access only the minimum amount of PHIpersonally identifiable information PII necessary B Logoff or lock your workstation when it is unattended C Promptly retrieve documents containing PHIPHI from the printer D All of this above.
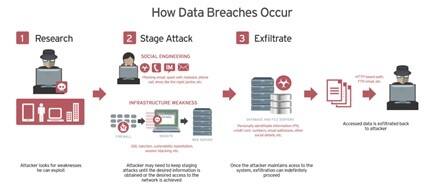
While the causes of breaches may vary the effects are very similar across the board. However these 30 best practices for preventing a data breach can reduce the risk and respond to an attack more effectively. Invest in security automation.
The following are high-level best practices for preventing breaches. In which of the following circumstances must an individual be given the opportunity to agree or object to the use and disclosure of their PHI. A breach can be the result of internal or external attackers.
1800-1 Securing Electronic Health Records on Mobile Devices. Established a national set of standards for the protection of PHI that is created received maintained or transmitted in electronic media by a HIPAA covered entity CE or business associate BA b. 20 Which of the following are breach prevention best practices.
Cloud and Hybrid. Public Health Nigeria Public Health Nigeria an Interdisciplinary public health movement focused on health education advancing fair public health policies promoting fitness healthy diets responsible behavior community health and general wellbeing. All of this above answer.
Access only the minimum amount of PHIpersonally identifiable information PII necessary. In which of the following circumstances must an individual be given the opportunity to agree or object to the use and disclosure of their PHI. Finding the best location for building a new plant is an example of a structured.
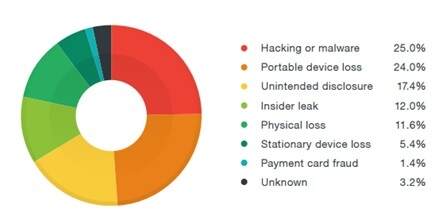
The healthcare industry experiences more data breaches confirmed data disclosure than any other industry in the United States accounting for more than 24 of all breaches. All of this above. 1800-3 Attribute Based Access Control.
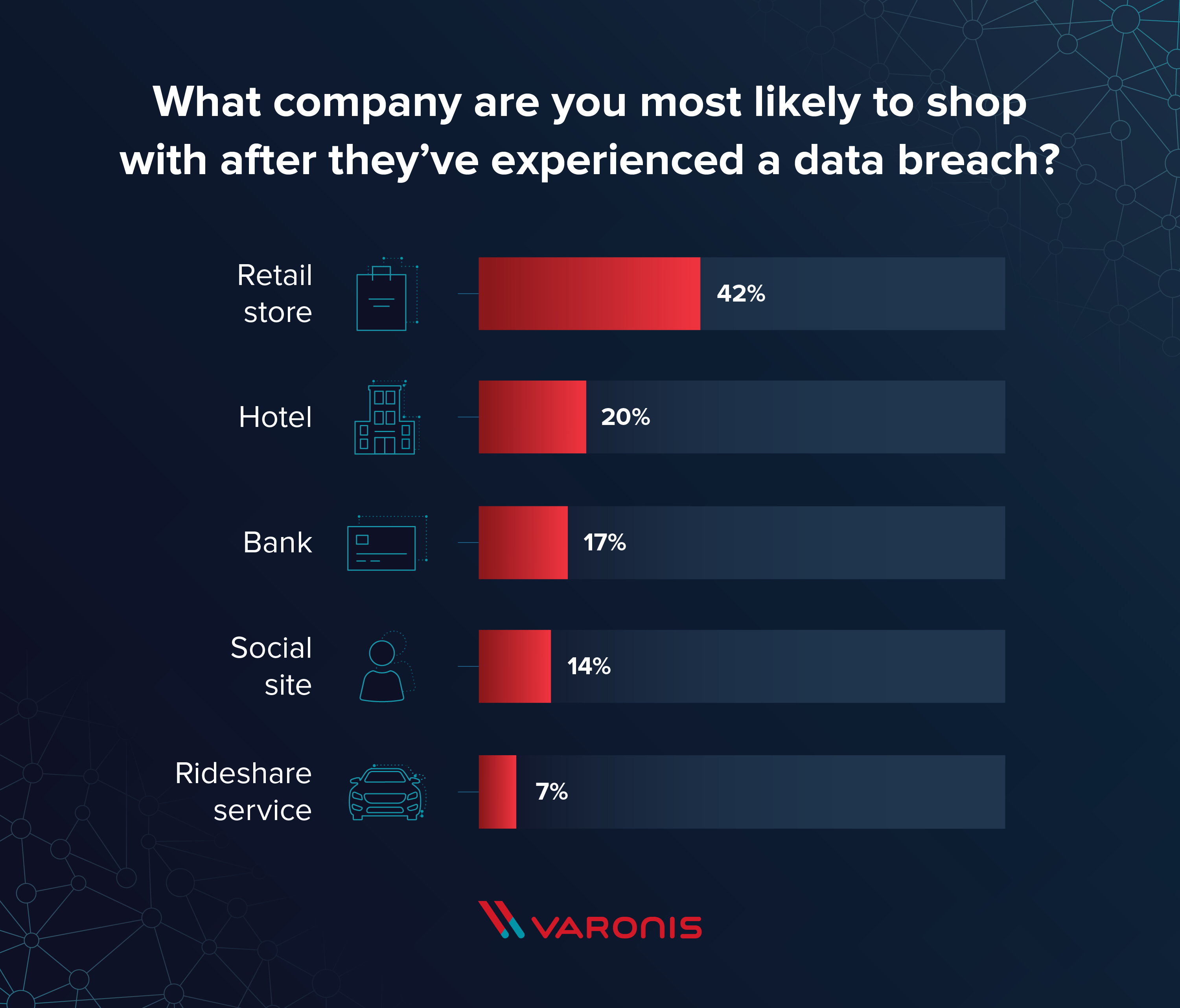
Analyzing Company Reputation After A Data Breach

Top 4 Human Errors In Cyber Security How To Prevent Employee Mistakes Ekran System
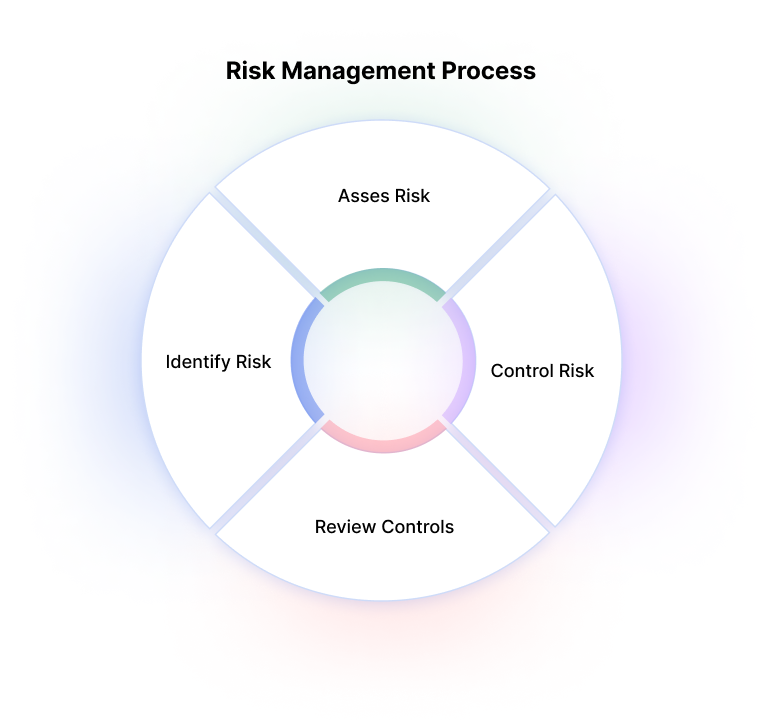
Cybersecurity Risk Management Frameworks Analysis Assessment Imperva

6 Steps To Developing A Data Breach Response Plan Spectral

How To Prevent Data Breaches In 2022 Upguard

6 Most Common Causes Of Data Leaks In 2022 Upguard
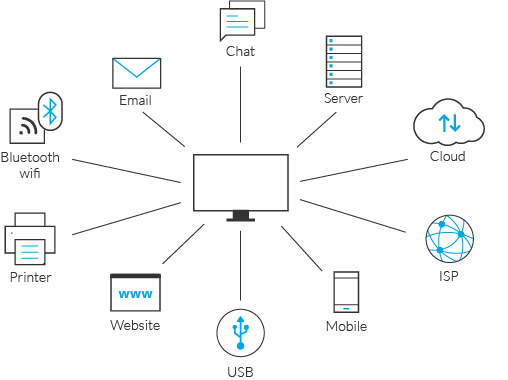
What Is Data Loss Prevention Dlp Data Leakage Mitigation Imperva
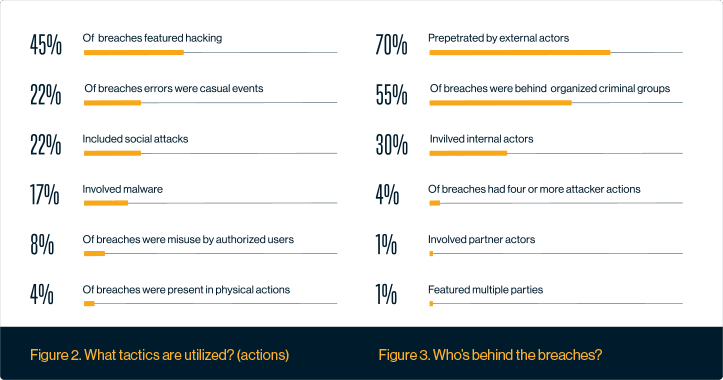
Data Breaches Complete Guide To Threats Tools And Tactics

Board Oversight Of Cyber Risks And Cybersecurity Imd Article
5 Best Practices For Data Breach Prevention Endpoint Protector

Certificate Management Best Practices Checklist Hashed Out By The Ssl Store

6 Most Common Causes Of Data Leaks In 2022 Upguard

7 Data Loss Prevention Best Practices Expert Explains Purplesec Youtube

Analyzing Company Reputation After A Data Breach

Preventing Hipaa Data Breaches Case Studies And Best Practices